I’ve written before about the safety of public WiFi networks, and I came to the conclusion that in general, they’re not safe, especially the “Free WiFi” at your local coffee shop.
Obviously the safest way is to not use these networks at all and to use the cellular network on your phone, but that will eat into your data.
So what are your options?
Well you could use a VPN like IpVanish (#CommissionsEarned) which is great, but you have to install special client software on your machine. And if it’s a work machine that you’re working on, you might not have local admin rights to install.
Another solution, which I’m going to go through is to use what is known as a SOCKS proxy will be be used together with SSH.
If this seems scary, don’t worry as it’s not as complicated as it sounds, and I’ll explain step-by-step what it is and how to get started.
By the end of this tutorial, you’ll have a secure and encrypted way of browsing the Internet without someone in the middle being able to watch and snoop on your traffic. It’s all too easy these days for hackers to use free tools like Firesheep to access your social media and run riot. So I’m going to share this tip with you and help to keep you safe online.
On top of that, I think this is a great weekend DIY project and an opportunity to learn about things like setting up your own Virtual Private Server (if you haven’t got one already), SSH and basic Linux commands.
So let’s begin shall we?
What is a SOCKS proxy?
Before we get into the nitty gritty, the SOCKS proxy concept is worth a little explanation.
A SOCKS server is basically a general purpose proxy server that first of all establishes a TCP connection with another server on behalf of a client and from then on routes all your traffic back and forth between your client and an external server (which could be a website).
A SOCKS proxy server can work with any network protocol, although we’ll be using it with SSH. And in SOCKS version 5 (which again, we’ll be using) you get extra support for security and UDP.
The SOCKS server doesn’t do anything clever with your traffic, it simply passes your traffic between your client and the server that you wish to connect to.
How it works
SOCKS is basically a client/server model. So your laptop or computer must have a SOCKS client installed onto it (if it’s Windows, then that’s probably PuTTY and Firefox).
The SOCKS client first of all establishes a connection to a SOCKS server and the SOCKS protocol then allows for authentication and logging of the connection requests.
So effectively your are providing the PROXY server with the requests you wish to make and it is the PROXY server that talks to the external server. So the external server is only ever aware of the existence of the PROXY server which is why it is good in terms of privacy.
How to set up a SOCKS proxy with SSH
OK, so before you can actually get started with this method, there’s a few things that you need first. Here they are:
Prerequisites
- A Virtual Private Server (VPS). You need a server which runs Linux (any version) such as Ubuntu 16.04 and you also need to be able to logon to your server with SSH.
- Firefox web browser (everyone, free)
- PuTTY to login to your server (Windows users only, Mac OS/Linux users already have the tools built into the Operating System).
Now, let’s talk about the Virtual Private Server.
Virtual Private Server (VPS)
If you don’t already one, get yourself a VPS. I recommend Linode (#CommissionsEarned) for this and I use it to host Bonkers About Tech – check out my full review of Linode. You can get yourself a decent Linode server for just $5/month.
Once you’ve signed up, read this step-by-step guide on getting started with Linode. One of the best things about Linode is that their documentation is second to none and so are their YouTube videos, so it’s very easy to get up and running even for a complete beginner.
Once you have a server and can login via SSH then move on to the next step.
Setting up the SSH Tunnel
Now there’s two ways of going about this depending on whether you’re a Windows user or not. If you’re Windows user, then you can skip this first bit. If you’re a Mac OS X/Linux user, then keep reading.
First of all though, make sure you have setup an SSH key so that you can access your server. For extra security, you can also setup a passphrase which must be entered once you’ve logged onto your server by SSH.
Setting up the SSH Tunnel – Mac OS X/Linux
Once you’re setup properly with SSH open up the terminal on Mac OS X (Applications -> Utilities) and enter the following command to set up the tunnel:
$ ssh -D 1026 -f -C -q -N [email protected]
Here’s an explanation of what all that means:
-D: This basically tells SSH to set up a SOCKS proxy on the port number that immediately follows. Port numbers range between 1025 and 65536. Port numbers up to 1024 are reserved for privileged services and are called well-known ports (or system ports).
-f: Requests SSH to go to the background just before command execution
-C: Requests compression of all data
-q: Enables quiet mode which causes most warning and diagnostic messages to be suppressed.
-N: Tells SSH not to execute remote commands once the tunnel is set up.
For more information about SSH and Mac OS X, check out the Apple developer documentation.
Obviously replace name@yourdomain with your own sudo user and domain name. If you haven’t got a domain name, then you can just use your server’s IP address.
Now because the command will run quietly and warning messages etc are suppressed (like we instructed it to), when you execute the command you’ll arrive back at the command prompt again, so it doesn’t look like the process is running.
To double check that the process is actually running you can run the following command:
$ ps aux | grep ssh
And you should get something similar to the following where the number next to the user is the actual Process ID (PID).
baz 31197 0.0 0.1 95368 3340 ? ........
Closing the tunnel
If you wish to close the tunnel and stop Firefox from communicating via the proxy at any time, then you can use the command above to find out the PID and then kill it using the kill command.
So, if the command above reveals a PID of 31197, you can kill the process as follows:
$ sudo kill 31197
Setting up the SSH Tunnel – Windows
Setting up the SSH tunnel in Windows requires you to use PuTTY which is a desktop based SSH client. If you haven’t already downloaded it, you can download it from here.
You don’t need to actually install PuTTY you can just run the executable right out of the box.
Let’s look at how you can configure PuTTY to set up the tunnel:
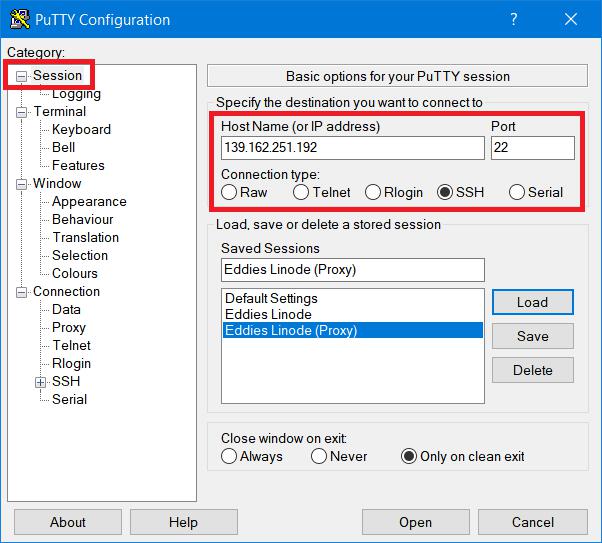
Instruction #1
Launch Putty and in the “Category” tree on the left hand side, select Session and enter your Host Name (or IP address). The port is 22 by default but SSH can be set up to use any port number, so you should enter it if it’s different. The SSH radio button is also selected by default, so leave it as is.
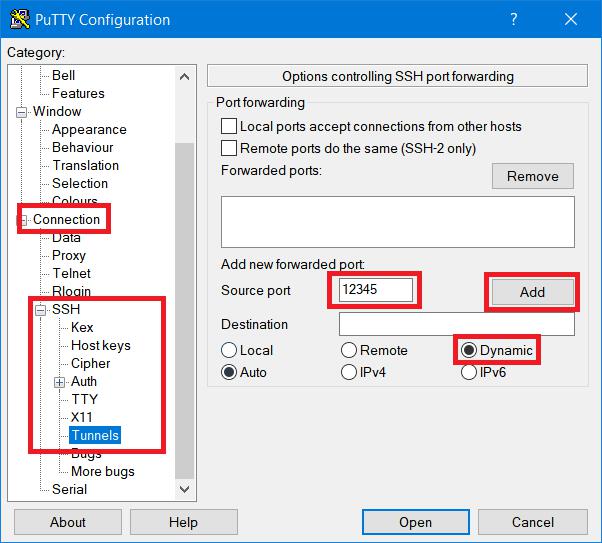
Instruction #2
In the tree on the left hand side, select Connection -> SSH – > Tunnels. Enter a number in source port (anything between 1025 and 65536 as I mentioned above). Finally check the radio button Dynamic.
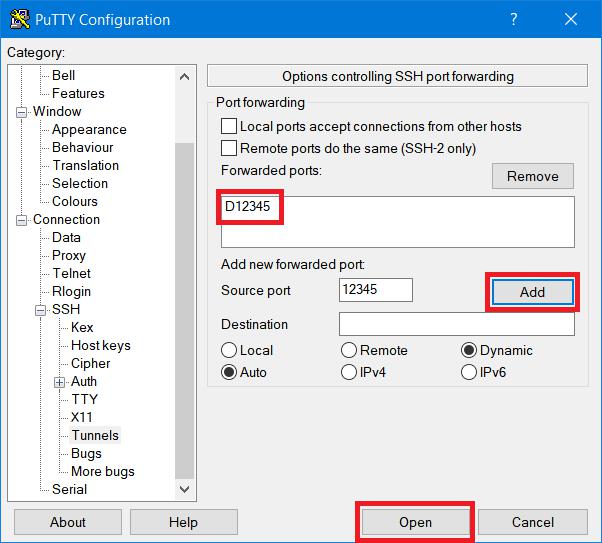
Instruction #3
Click the Add button and you should now see the port in the Forwarded ports text area.
Instruction #4
Finally click on the Open button. This will cause another window to popup asking for the password to your VPS. Once you’ve entered the password, you’ll be logged into your VPS and the tunnel will created. Minimize the PuTTY widow and move onto the next section.
Closing the tunnel
Closing the tunnel is even simpler in Windows, all you have to do is close the PuTTY window that you used to create the tunnel. Simple as that.
Configuring Firefox to use your SSH Tunnel
Now that you’ve setup your tunnel, it’s time to start using using it to browse the Internet.
To do this we’re going to set up Firefox to use our SOCKS proxy server. It is possible to do it in other browsers too, but some may require a browser extension. For example you can use this Chrome extension to use a PROXY server.
Instruction #5
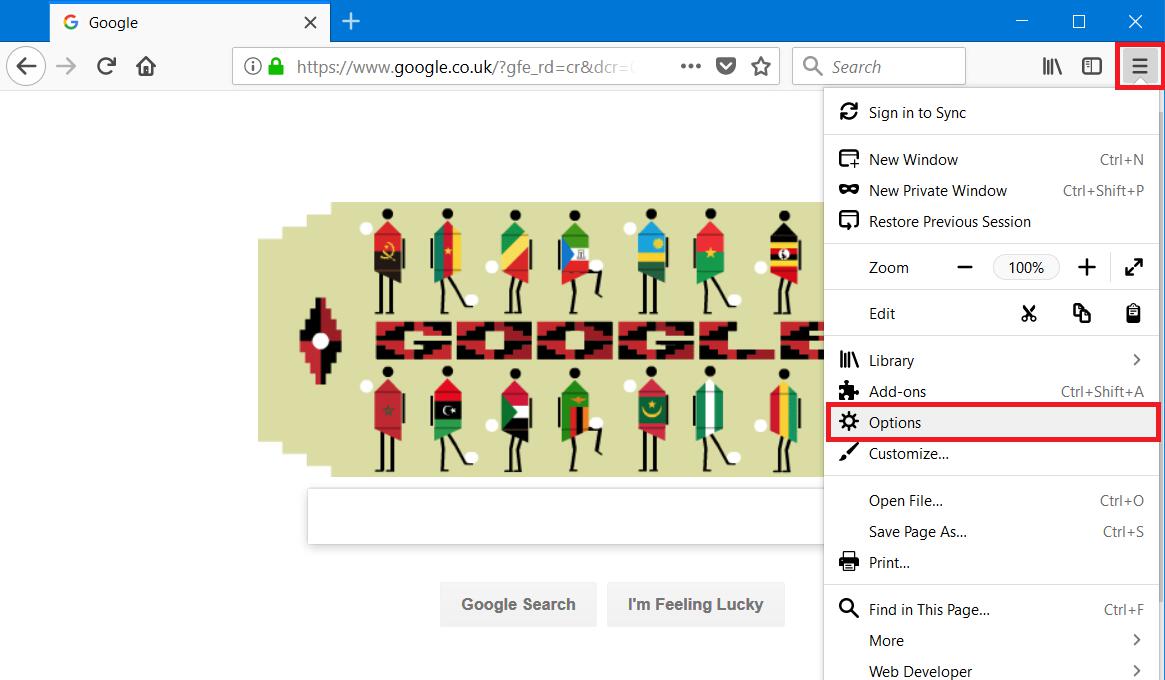
Open Firefox and click “Open menu” which is the “hamburger” menu in the top right of the browser and click on Options.
Instruction #6
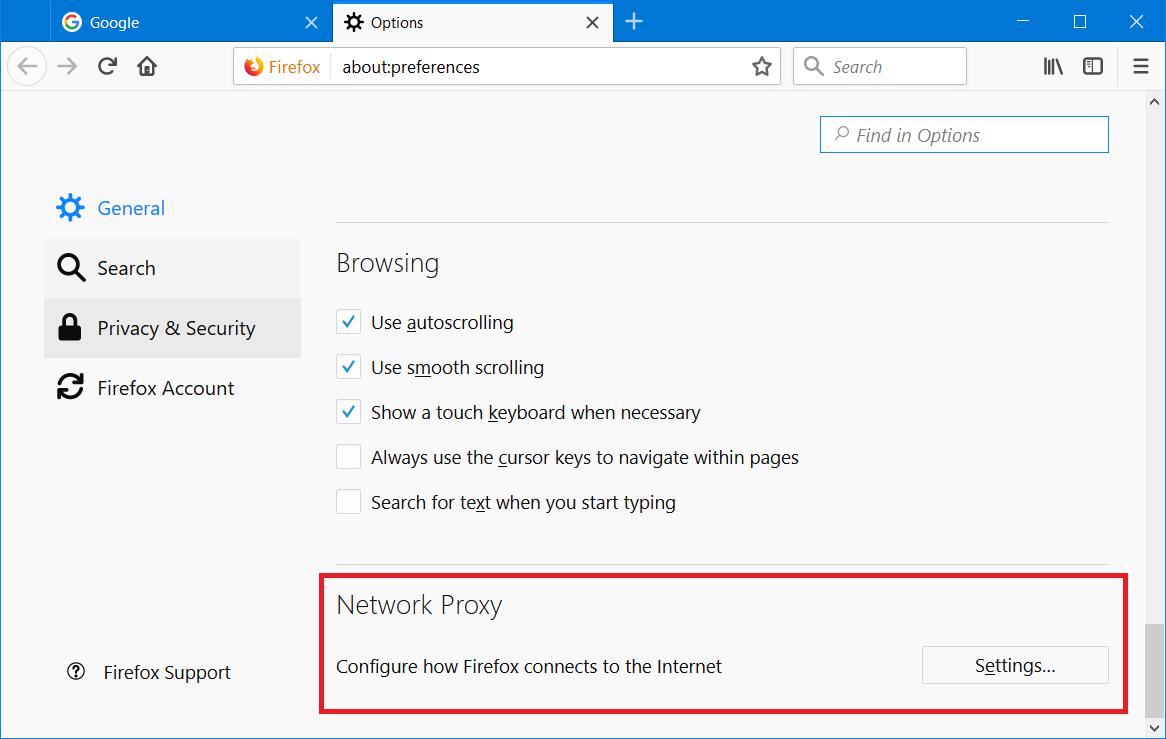
Scroll down to the very bottom of the Options page and in the Network Proxy section, click Settings…
Instruction #7
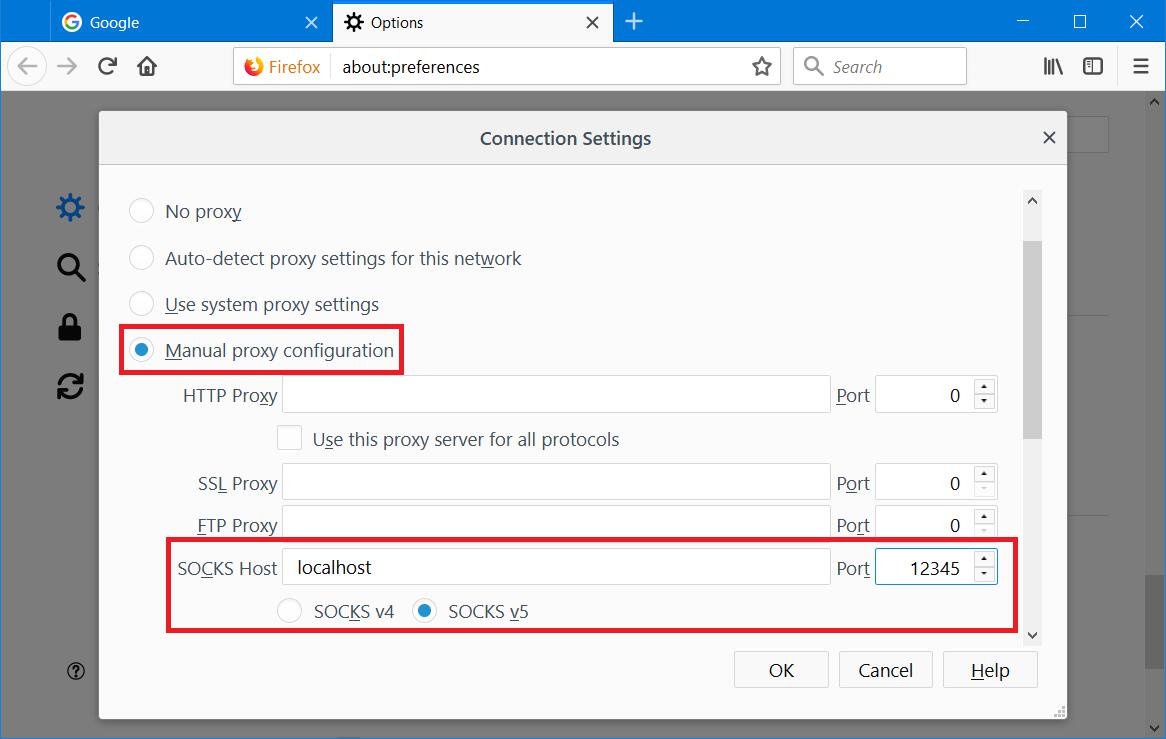
In the Configure Proxies to Access the Internet section, select Manual proxy configuration and in the SOCKS Host text field, enter localhost (or 127.0.0.1) and the port that you chose in instruction #2. Make sure that the SOCKS v5 radio button is selected (it should be by default) and click OK.
How to check your VPS PROXY tunnel is working
To check that everything is working as expected, simply Google “what is my IP” in Firefox and it should tell you the IP address of your VPS.
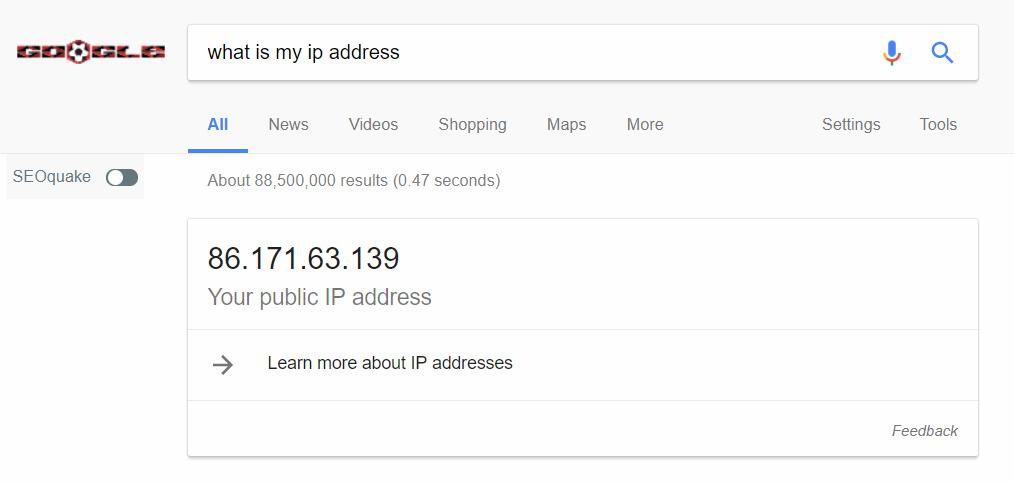
So for example, without using my proxy (in Chrome for example) you can see that my IP address is 86.171.63.139:
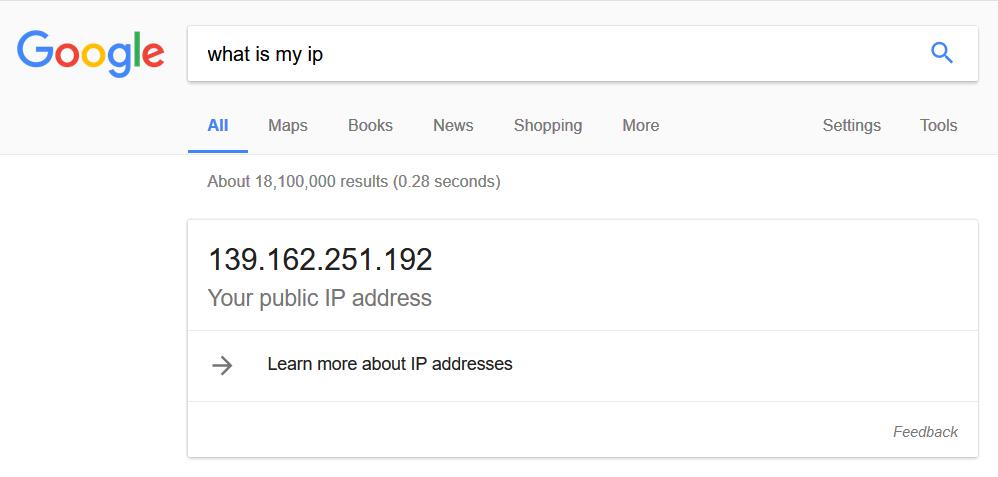
In Firefox (using the proxy) you can see that my IP address is now 139.162.251.192 which is the IP address of bonkersabouttech.com, I now appear to be in London in a Linode datacenter somewhere!
Securing DNS
Now although your web traffic will be encrypted and forwarded and therefore “appear” to a particular website that you are requesting pages from a different IP address, your DNS lookups will actually be carried out by the network that you’re on, which won’t be private.
Fortunately, there’s a solution for that too! Follow these instructions to find out how:
Instruction #8
Open Firefox and in the address bar type about:config to access the browser’s internal settings. You need to be careful with these settings as you could screw over your browser, which is reflected in the warning that pops up. Click I accept the risk and move onto the next instruction.
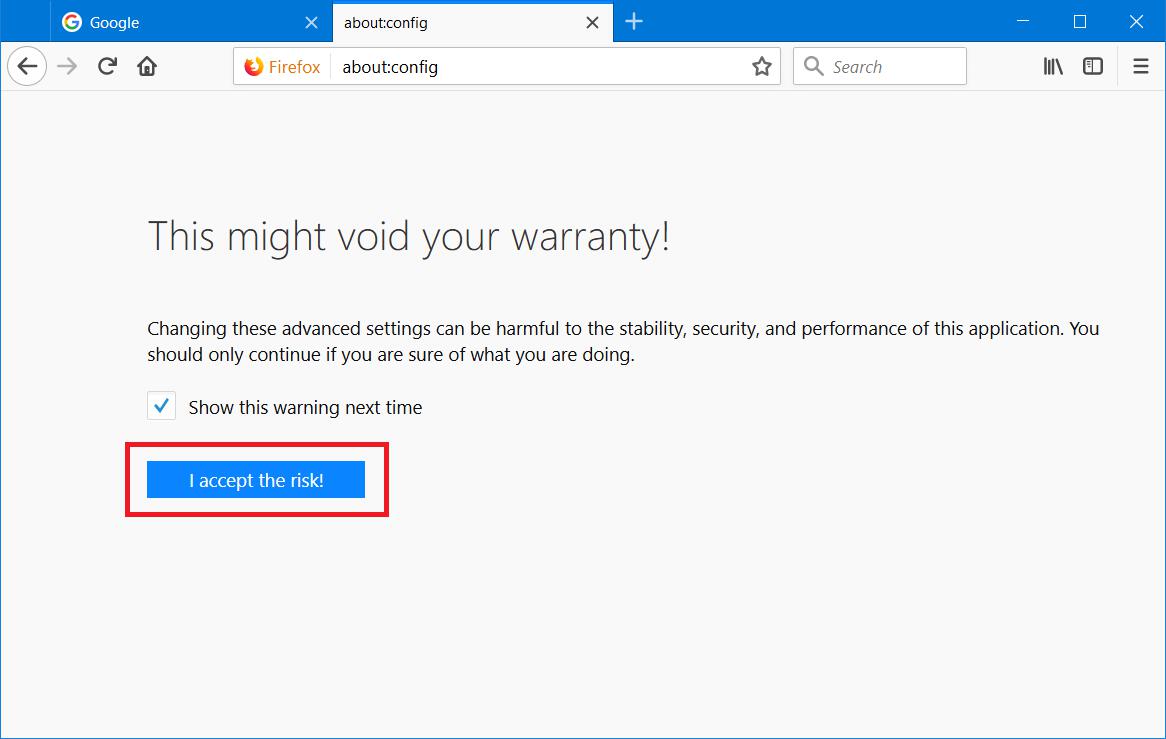
Instruction #9
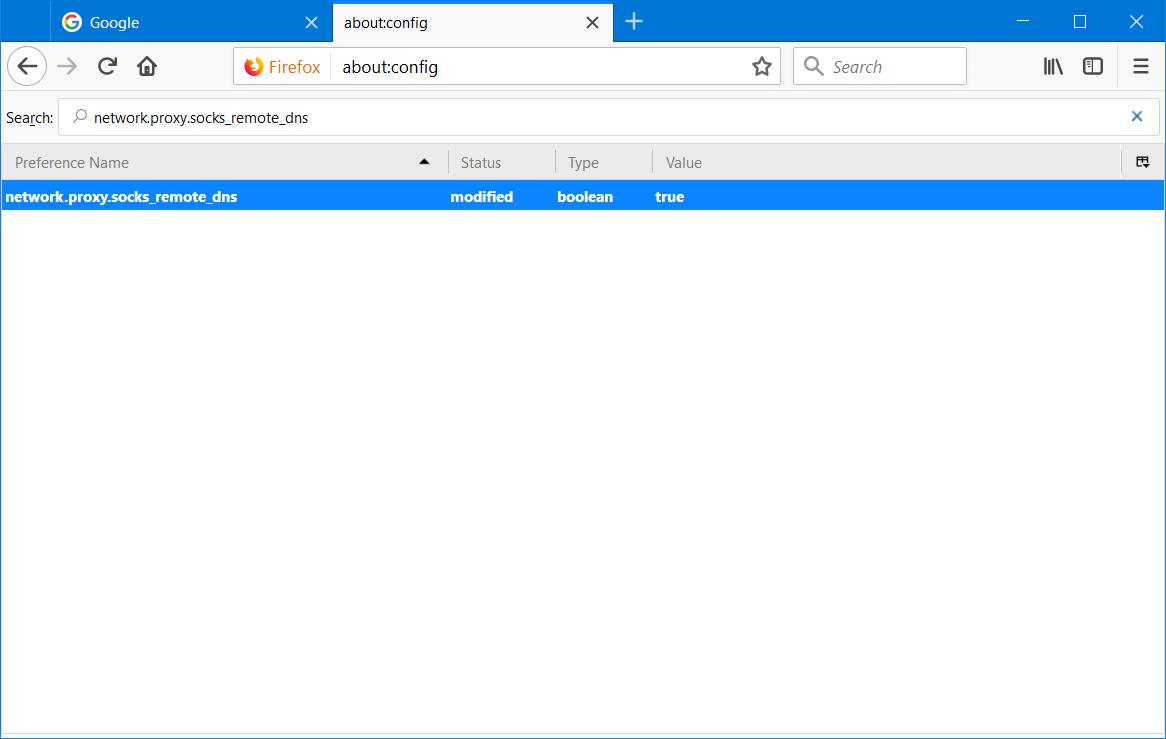
In the search bar at the top, type network.proxy.socks_remote_dns
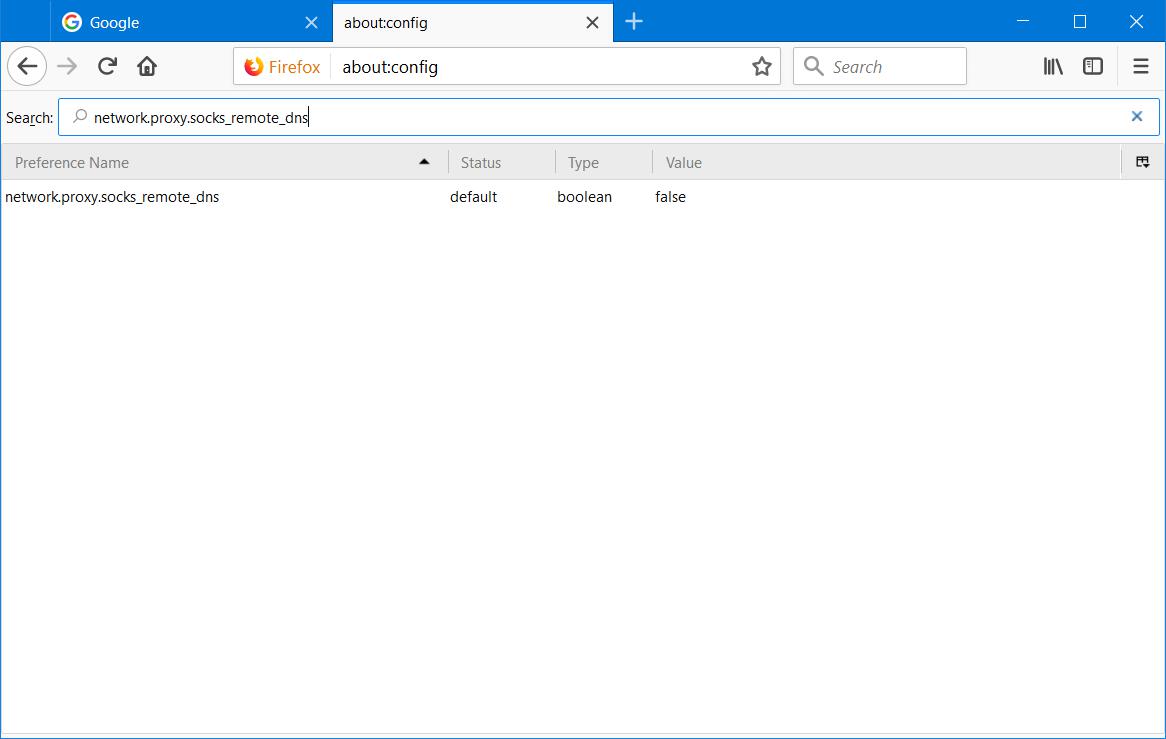
Instruction #10
Double click the whole network.proxy.socks_remote_dns line and you’ll notice that the all the text turns bold and more importantly, the value will change from false (the default value) to true. The status will also change from default to modified.
And that is it, Firefox will now proxy DNS requests instead of trying to resolve them locally.
Caveats
Using a VPS as a proxy is definitely a great way to enjoy a secure connection to the Internet but it’s not without its downfalls. Let’s look at a few of them:
- SSH access might be blocked – You may not be able to access your server on port 22 as it may have been blocked on the network you’re on. If this is the case you can run your SSH server on a different port, which will definitely be open like port 80 (HTTP) for example. With Linode you can even access your Linode shell from a web browser.
- Browsing maybe slower – Your Internet speeds may be affected by browsing using a proxy but I think this is worth it, especially if your privacy is at risk on a public Wi-Fi network.
- You’re restricted to a single IP address – One of the benefits of a VPN is having access to many different servers which will give you a different IP address each time you connect. With this solution, you’re restricted to a single IP address which will remain static for the life of your VPS.
- Only the browsers that are set up to use your proxy are protected – So in other words, any apps that you use or any other means of connecting to the Internet will not be protected by your PROXY server. You need to configure things on a case-by-case basis to use your PROXY server. If you want all your Internet traffic protecting, you need to use a VPN.
Wrapping up
So that’s it guys, a simple yet effective way to protect your privacy online. If all you want to do is keep your browsing private by encrypting your traffic, then this is a good DIY option, and it’s cheap too at just $5/month with Linode. If you want to protect all your traffic (all apps, games, browsers etc) then you need to get yourself a VPN (#CommissionsEarned).
As always, let me know how you get on and if you have any issues, just let me know in the comments at the end of the post.
Cheers!
